Content Security Policy (CSP) support
Content Security Policy (CSP) can be set by application and servers to tighten security by:
- Only allowing resources to be loaded from pre-defined sources
- Only allowing XHR calls to pre-defined sources
- Disabling inline JavaScript in HTML
This conflicts with the UXM Web Agent, because it's normally loaded from the UXM servers at ://repo.mcg.dk/uxm/web/latest/uxm_web_agent.min.js and data is send to the cloud collector customerInstance.uxmapp.com
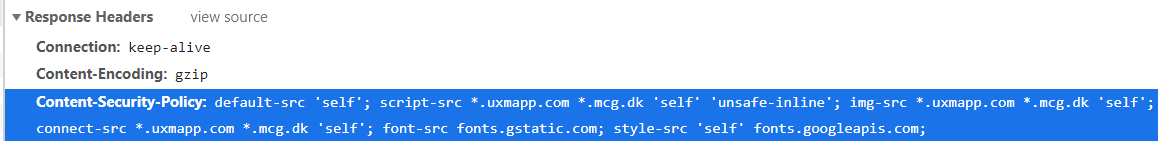
It can be seen in the headers set by the main document:
It can also be set in the HTML metadata which can be seen in "View Source"
The following configuration of application/servers can be done to support the UXM Web agent by adding the CSP directive below to your CSP configuration.
script-src \*.uxmapp.com \*.mcg.dk 'self' 'unsafe-inline'; img-src \*.uxmapp.com
\*.mcg.dk 'self'; connect-src \*.uxmapp.com \*.mcg.dk 'self';
The headers will then look like the image below:
'unsafe-inline' can be avoided if you SHA256 encode the content of the script tag, Google Chrome developer tools shows the SHA256, for example:
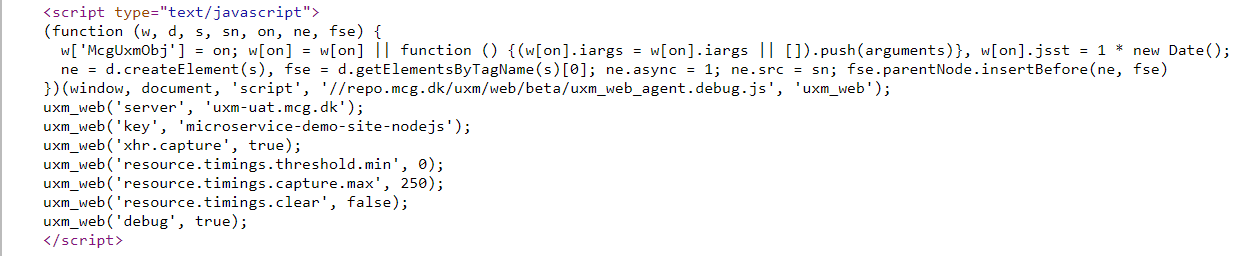
Becomes:
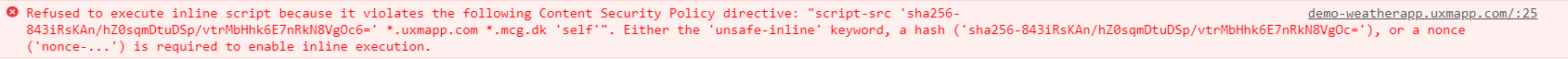
Adding Chromes recommended hash to the CSP policy allows the script to be executed without 'unsafe-inline' directive.
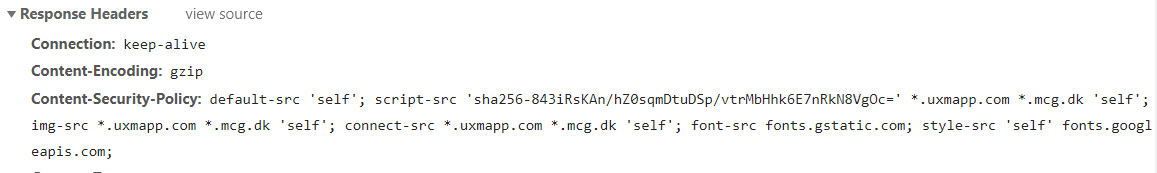
Please avoid using dynamic values in the config, like trace.id, this will break the SHA256 because new values is generated during each load of the page.
Troubleshooting
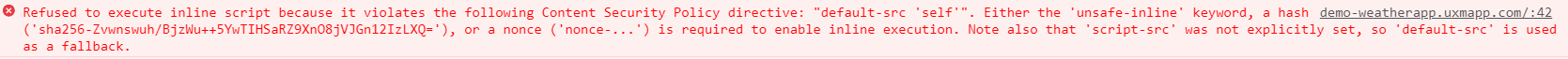
Loading of UXM Web agent JavaScript fails due to CSP
- Allow UXM Web agent JavaScript to be loaded from *.mcg.dk or *.uxmapp.com via (script-src *.uxmapp.com *.mcg.dk 'self')
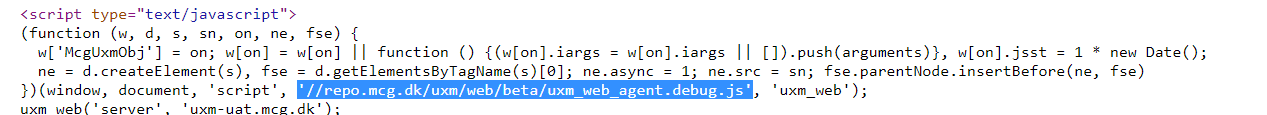
 2. Move UXM Web agent JavaScript local to server
2. Move UXM Web agent JavaScript local to server
You can copy the JavaScript locally to your server and load it from there by altering the load path:
Sending of results fails due to CSP
The developer console in FireFox and Chrome will show the CSP error "Refused to connect to 'https://x.uxmapp.com/data/browser/' because it violates the following Content Security Policy directive: "default-src 'self'". Note that 'connect-src' was not explicitly set, so 'default-src' is used as a fallback."
![]()
You have set incorrect img-src and connect-src domain names in your CSP policy, add *.uxmapp.com or *.mcg.dk.
img-src \*.uxmapp.com \*.mcg.dk 'self'; connect-src \*.uxmapp.com \*.mcg.dk 'self';